
China Regains 14 % of Global Bitcoin Mining Share in Surprise Revival
25 Nov 2025
China’s Bitcoin mining resurges to around 14% of global share, driven by cheap power and rig demand, even though the 2021 ban still formally stands.

As Stablecoins Boom, Brazil Considers a New Tax on Crypto Transfers
18 Nov 2025
Brazil is considering extending its IOF tax to cross-border crypto payments, aiming to close a regulatory gap as stablecoin use surges nationwide.

Bank of England Signals Softer Approach to Stablecoins Under New Proposals
11 Nov 2025
Bank of England proposes new stablecoin rules allowing 60% reserve investment in government debt while keeping strict holding limits.

JPYC Launches the World’s First Yen-Backed Stablecoin in Japan
28 Oct 2025
Japan’s JPYC launches the world’s first yen-backed stablecoin, aiming to challenge dollar-pegged dominance in the global crypto market.

Evernorth and Armada Acquisition Corp II to Merge - Will Use $1 Billion to Create an XRP Treasury
22 Oct 2025
Evernorth Holdings Inc. and Armada Acquisition Corp II will merge to create a new company. The company will use $1 billion in gross proceeds to buy XRP.

China Tells Its Tech Giants to Halt Stablecoin Plans Amid Regulatory Review
21 Oct 2025
Beijing halts private stablecoin projects by tech giants, signaling tighter control as China pushes ahead with its digital yuan strategy.

Coinbase Backs CoinDCX at $2.45B Valuation, Expanding Its Presence in India’s Crypto Market
16 Oct 2025
Coinbase is expanding its footprint in India & The Middle East by making an investment in CoinDCX, a regional market leader and existing portfolio company.
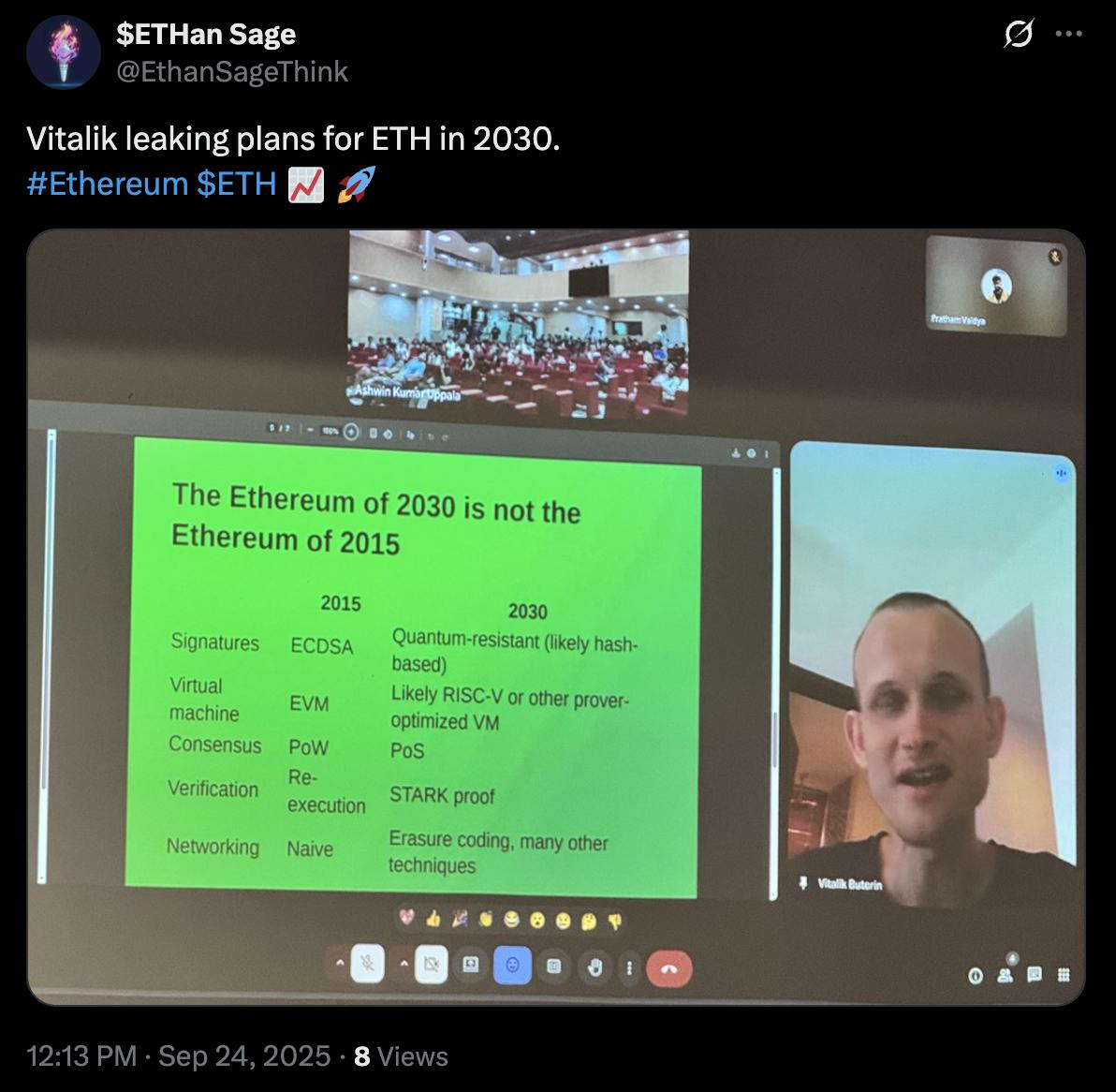
Ethereum 2030: Vitalik's Audacious Vision vs. Harsh Reality Check
24 Sept 2025
Vitalik Buterin hasn't been shy about painting bold futures for Ethereum. His latest roadmap for the next five years reads very ambitiously... it is achievable?

Critical Findings: Developer Crypto Challenges on Stack Overflow
29 Jul 2025
This study reveals developers' significant struggles with crypto, citing knowledge deficits and complex libraries as key issues.
